In this post, we present our new Burp Suite extension "TLS-Attacker".
Using this extension penetration testers and security researchers can assess the security of TLS server configurations directly from within Burp Suite.
The extension is based on the TLS-Attacker framework and the TLS-Scanner, both of which are developed by the Chair for Network and Data Security.
You can find the latest release of our extension at: https://github.com/RUB-NDS/TLS-Attacker-BurpExtension/releases

Furthermore, the extension allows fine-tuning for the configuration of the underlying TLS-Scanner. The two parameters parallelProbes and overallThreads can be used to improve the scan performance (at the cost of increased network load and resource usage).
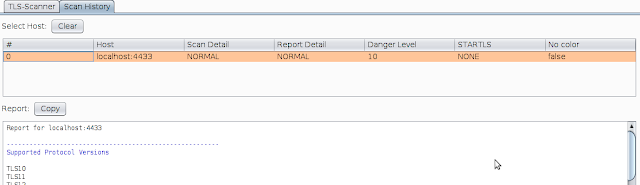
It is also possible to configure the granularity of the scan using Scan Detail and Danger Level. The level of detail contained in the returned scan report can also be controlled using the Report Detail setting.
Please refer to the GitHub repositories linked above for further details on configuration and usage of TLS-Scanner.
This is a combined work of Nurullah Erinola, Nils Engelbertz, David Herring, Juraj Somorovsky, Vladislav Mladenov, and Robert Merget. The research was supported by the European Commission through the FutureTrust project (grant 700542-Future-Trust-H2020-DS-2015-1).
If you would like to learn more about TLS, Juraj and Robert will give a TLS Training at Ruhrsec on the 27th of May 2019. There are still a few seats left.
More infoUsing this extension penetration testers and security researchers can assess the security of TLS server configurations directly from within Burp Suite.
The extension is based on the TLS-Attacker framework and the TLS-Scanner, both of which are developed by the Chair for Network and Data Security.
You can find the latest release of our extension at: https://github.com/RUB-NDS/TLS-Attacker-BurpExtension/releases
TLS-Scanner
Thanks to the seamless integration of the TLS-Scanner into the BurpSuite, the penetration tester only needs to configure a single parameter: the host to be scanned. After clicking the Scan button, the extension runs the default checks and responds with a report that allows penetration testers to quickly determine potential issues in the server's TLS configuration. Basic tests check the supported cipher suites and protocol versions. In addition, several known attacks on TLS are automatically evaluated, including Bleichenbacher's attack, Padding Oracles, and Invalid Curve attacks.

Furthermore, the extension allows fine-tuning for the configuration of the underlying TLS-Scanner. The two parameters parallelProbes and overallThreads can be used to improve the scan performance (at the cost of increased network load and resource usage).
It is also possible to configure the granularity of the scan using Scan Detail and Danger Level. The level of detail contained in the returned scan report can also be controlled using the Report Detail setting.
Please refer to the GitHub repositories linked above for further details on configuration and usage of TLS-Scanner.
Scan History
If several hosts are scanned, the Scan History tab keeps track of the preformed scans and is a useful tool when comparing the results of subsequent scans.
Additional functions will follow in later versions
Currently, we are working on integrating an at-a-glance rating mechanism to allow for easily estimating the security of a scanned host's TLS configuration.This is a combined work of Nurullah Erinola, Nils Engelbertz, David Herring, Juraj Somorovsky, Vladislav Mladenov, and Robert Merget. The research was supported by the European Commission through the FutureTrust project (grant 700542-Future-Trust-H2020-DS-2015-1).
If you would like to learn more about TLS, Juraj and Robert will give a TLS Training at Ruhrsec on the 27th of May 2019. There are still a few seats left.
- Hacking Apps
- Pentest Tools Website
- Hacking Tools For Kali Linux
- Hacker Tools List
- Hacker Tools Apk
- Hacking Tools For Mac
- Computer Hacker
- Black Hat Hacker Tools
- Hacking Tools Software
- Nsa Hacker Tools
- Hacker Tools 2020
- Hacking Tools Windows 10
- Wifi Hacker Tools For Windows
- Pentest Tools Find Subdomains
- Hacking Tools For Beginners
- Hacking Tools Free Download
- Hack Tools
- Hacker Tools List
- Hacker Tools For Ios
- Pentest Recon Tools
- Top Pentest Tools
- Hacking Tools For Beginners
- Best Pentesting Tools 2018
- Termux Hacking Tools 2019
- Hacker Tools Software
- Hack Tools For Windows
- How To Make Hacking Tools
- Hackers Toolbox
- Pentest Tools Download
- Hacker Tools For Ios
- Hacking App
- Growth Hacker Tools
- Hack Tools For Ubuntu
- Black Hat Hacker Tools
- Tools For Hacker
- Pentest Tools Port Scanner
- Pentest Tools Website
- Hack Tools 2019
- Hack Tools For Mac
- Ethical Hacker Tools
- Pentest Tools List
- Hacker Tools Free Download
- Hacking Tools Free Download
- Easy Hack Tools
- Hacking Tools Hardware
- Pentest Tools Website
- Pentest Tools Website Vulnerability
- Hacking Tools Windows
- Hak5 Tools
- Hack Tools Online
- Pentest Tools Linux
- Top Pentest Tools
- Android Hack Tools Github
- Hack Tools Pc
- Hacking Tools Github
- Pentest Tools Url Fuzzer
- Blackhat Hacker Tools
- World No 1 Hacker Software
- Pentest Tools Framework
- Pentest Reporting Tools
- Pentest Tools For Windows
- Wifi Hacker Tools For Windows
- Hack Tools Mac
- Hacks And Tools
- Hacking Tools Windows
- Pentest Automation Tools
- Pentest Tools For Ubuntu
- Game Hacking
- Pentest Tools Find Subdomains
- Nsa Hacker Tools
- Pentest Tools Review
- Game Hacking
- Hacking Tools Download
- Hack Tools
- How To Make Hacking Tools
- What Are Hacking Tools
- Hacker Tools 2020
- Pentest Tools Alternative
- Hacker Tools 2020
- Growth Hacker Tools
- Hak5 Tools
- Hacking Tools Github
- What Are Hacking Tools
- Hacker Security Tools
- How To Make Hacking Tools
- Hacker Security Tools
- Pentest Tools Android
- Hack App
- Pentest Tools Bluekeep
- Tools 4 Hack
- Hacking Apps
- Hacking Tools For Windows
- Hak5 Tools
- Pentest Tools Download
- Easy Hack Tools
- Beginner Hacker Tools
- Hacking Tools And Software
- Hacker Tools Online
- Hack Tool Apk
- Pentest Box Tools Download
- Game Hacking
- Pentest Tools For Android
- Blackhat Hacker Tools
- Pentest Reporting Tools
- Pentest Tools Find Subdomains
- Install Pentest Tools Ubuntu
- Hacker Tools 2019
- Hacker Tool Kit
- Tools Used For Hacking
- Pentest Tools Linux
- Pentest Tools Framework
- Hacker
- Pentest Tools Free
- Hacking Tools For Mac
- Hacking Tools Download
- Best Hacking Tools 2019
- Hacker Tools For Mac
- Hack Tools Github
- Pentest Tools Website
- Pentest Tools Find Subdomains
- Hacking Tools Download
- Hacker Tools 2019
- Hacker Tools For Pc
- Nsa Hack Tools
- Hacks And Tools
- Pentest Tools Free
- Pentest Tools For Android
- Tools For Hacker
- Computer Hacker
- Physical Pentest Tools
- Wifi Hacker Tools For Windows
- Ethical Hacker Tools
- Install Pentest Tools Ubuntu
- Hacking Tools Free Download
- Android Hack Tools Github
- Install Pentest Tools Ubuntu
- Hacking Tools For Mac
- Hacker Tools 2019
- Nsa Hacker Tools
- Hacking Tools Name
- Hacking Tools Software
- What Is Hacking Tools
- Hacking Tools For Windows Free Download
- Hack Tool Apk No Root
- Hack Tools For Pc
- Hacking Tools Hardware
- Hacking Tools For Games
- Blackhat Hacker Tools
- Android Hack Tools Github
- Hacking App
- Beginner Hacker Tools
- Hacking Tools Hardware
- Hacking Tools For Pc
- Hacking Tools Windows 10
- Pentest Tools Website Vulnerability
- Hacking Tools Hardware
- Tools For Hacker
- Hacker Tools Hardware
- Hack Tool Apk No Root
- Hacker Tools 2019
- Hacker Tools For Mac
- Hack Tools
- Hacker
- Hacks And Tools
- Github Hacking Tools
- How To Install Pentest Tools In Ubuntu
- Hack Tools For Games
- Hacker Security Tools
- Hacking Tools 2020
- Hack App
- Hack Tools Github
- Best Hacking Tools 2020
- Best Pentesting Tools 2018
No comments:
Post a Comment